# Configuring OAuth via Keycloak
KISTERS WISKI deploys Keycloak (opens new window) as Identity Provider. In order to configure Keycloak for TISGraph, follow this guide:
# Create Client in Keycloak
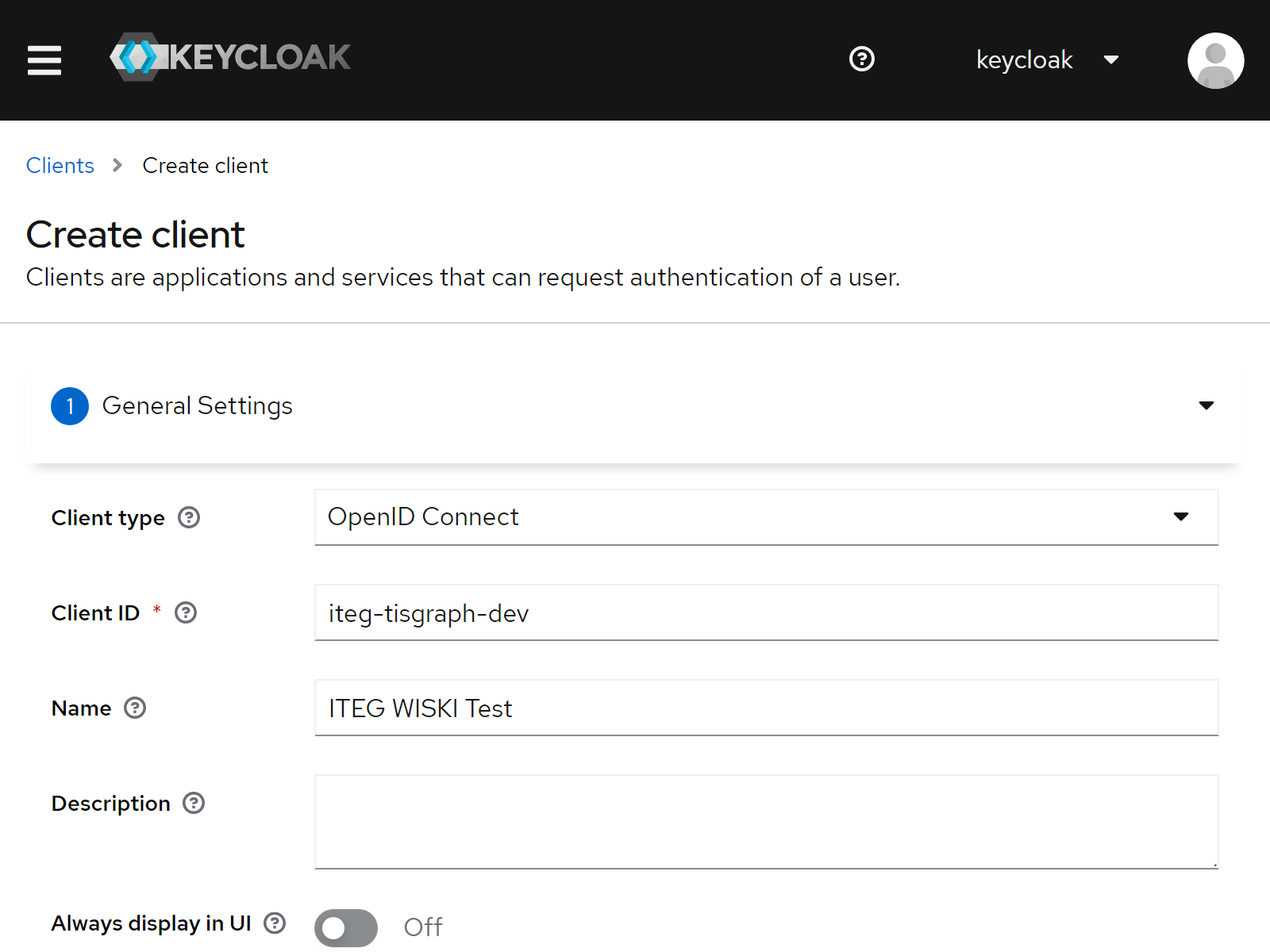
Firstly, navigate to https://wiski.example.com:7415/admin/master/console/#/kisters-water-default/clients and click "Create client".
In the wizard, configure the following
| Step. Name | Value |
|---|---|
| 1. Client type | OpenID Connect |
| 1. Client ID | iteg-tisgraph-dev |
| 1. Name | ITEG WISKI Test |
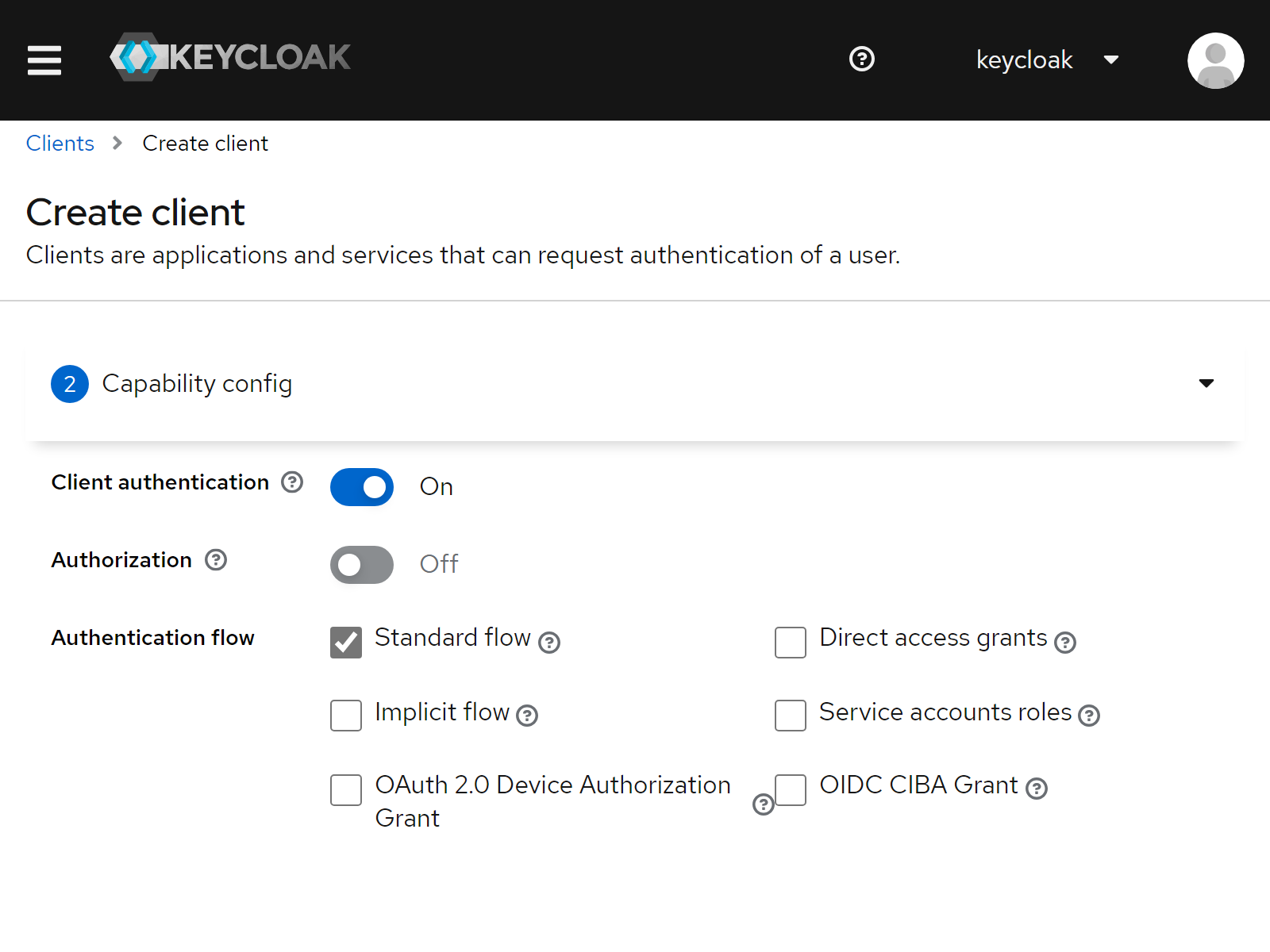
| 2. Client authentication | On |
| 2. Standard flow | On |
| 2. Direct access grants | Off |
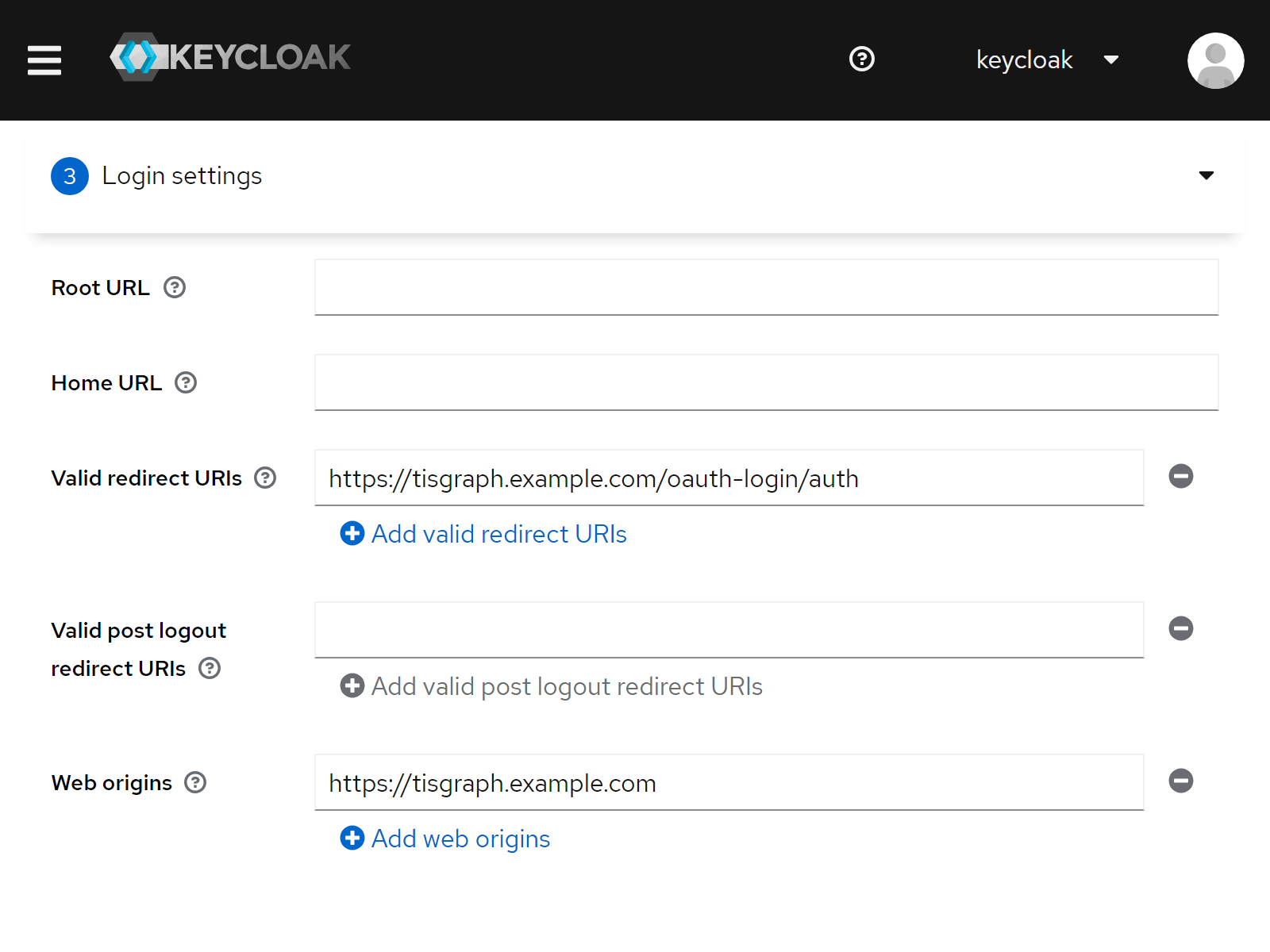
| 3. Root URL | <empty> |
| 3. Home URL | <empty> |
| 3. Valid redirect URIs | https://tisgraph.example.com/oauth-login/auth |
| 3. Web origins | https://tisgraph.example.com |
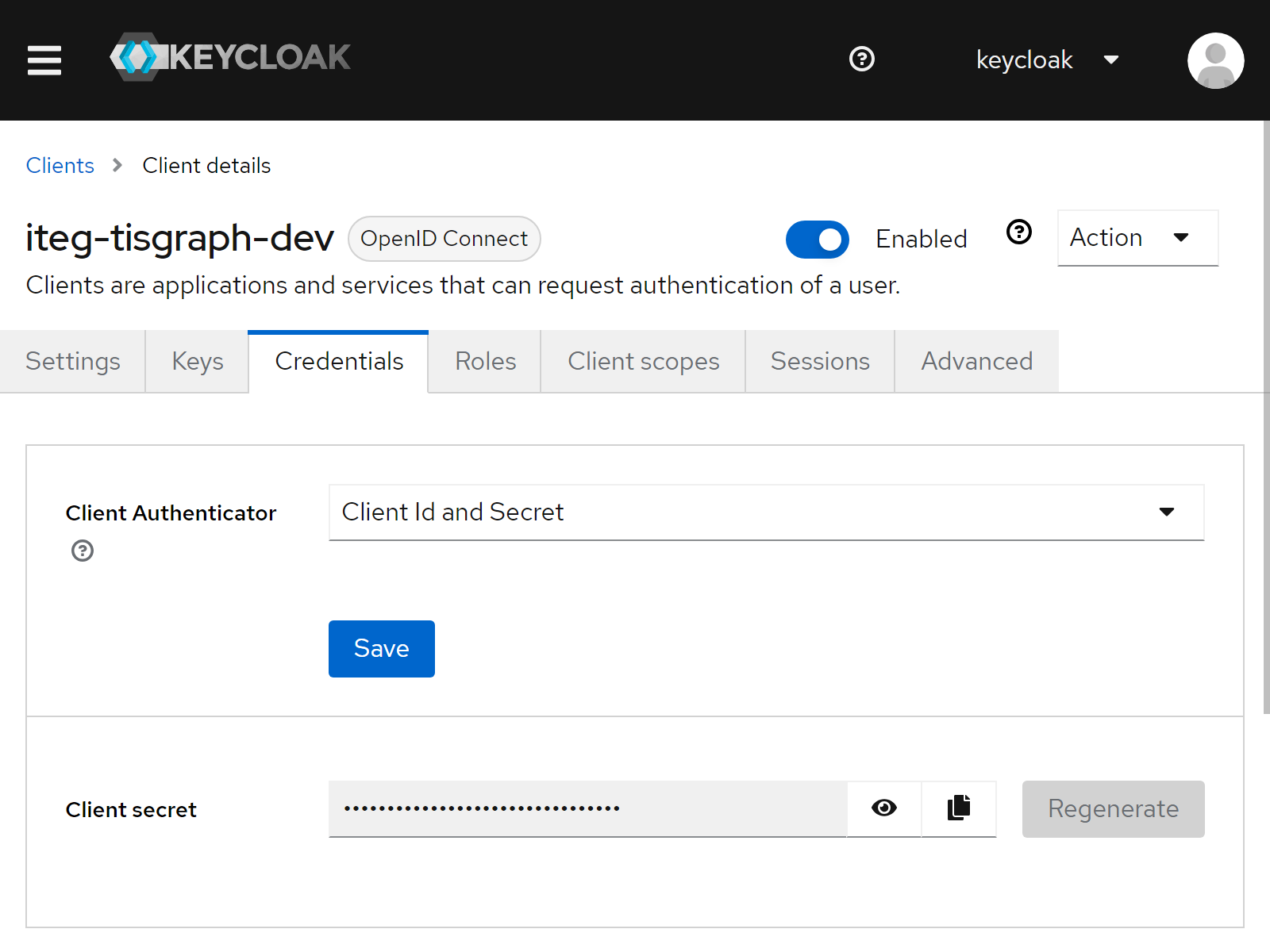
Navigate to the newly created client, open the tab "Credentials", and copy the "Client secret" to the clipboard.
# Configure TISGraph
Configure org.clazzes.login.oauth. In at.iteg.tis.graph, configure users.suPrincipal and delegateLoginMechanism and apiSecurityContext. Open https://tisgraph.example.com/oauth-login/login in order to try or debug the OAuth authentication.
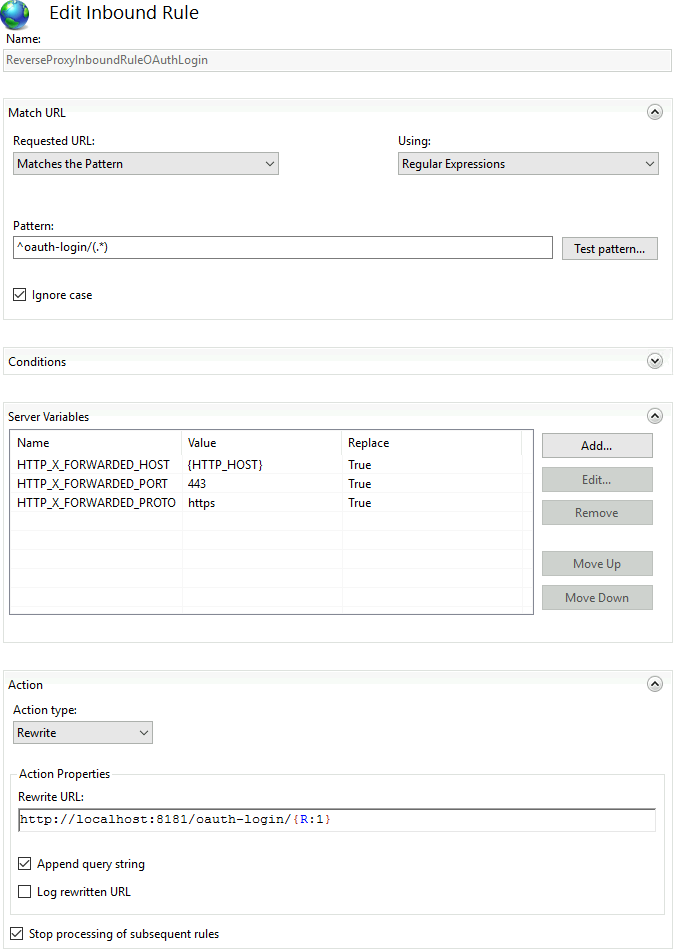
# Configure IIS
If the IIS (Internet Information Services for Windows Server) is used as reverse proxy, make sure that /oauth-login is proxied to TISGraph running on localhost:8181. Furthermore, make sure that the HTTP headers HTTP_X_FORWARDED_HOST, HTTP_X_FORWARDED_PORT, HTTP_X_FORWARDED_PROTO are set correctly. This is necessary as TISGraph needs to construct a redirect_uri for the authentication flow.
<rule name="ReverseProxyInboundRuleOAuthLogin" stopProcessing="true">
<match url="^oauth-login/(.*)" />
<action type="Rewrite" url="http://localhost:8181/oauth-login/{R:1}" />
<serverVariables>
<set name="HTTP_X_FORWARDED_HOST" value="{HTTP_HOST}" />
<set name="HTTP_X_FORWARDED_PORT" value="443" />
<set name="HTTP_X_FORWARDED_PROTO" value="https" />
</serverVariables>
</rule>